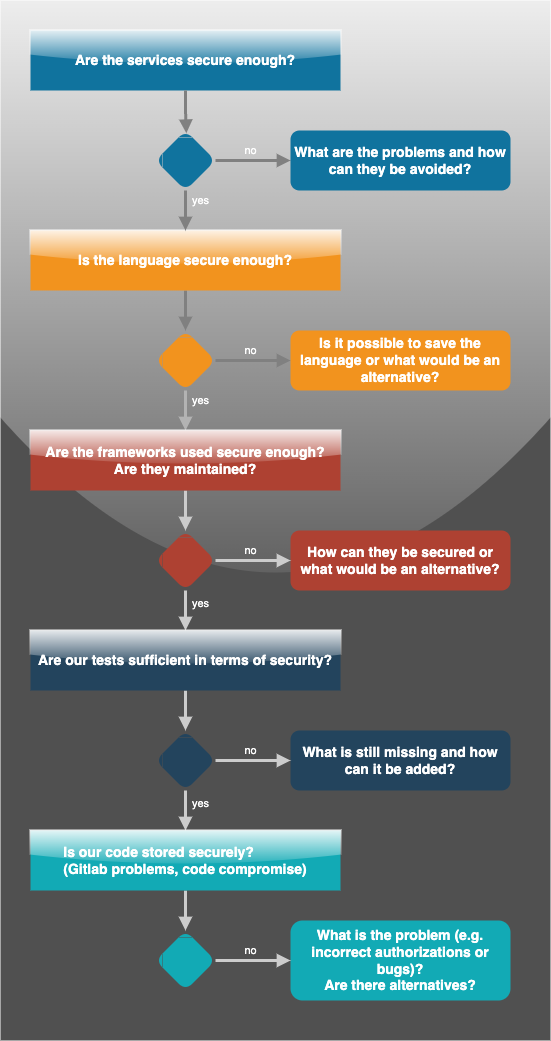
Secure Software Development Process
We use several tools and processes for the development of the software in order to be able to deliver an error-free and secure solution.
Process
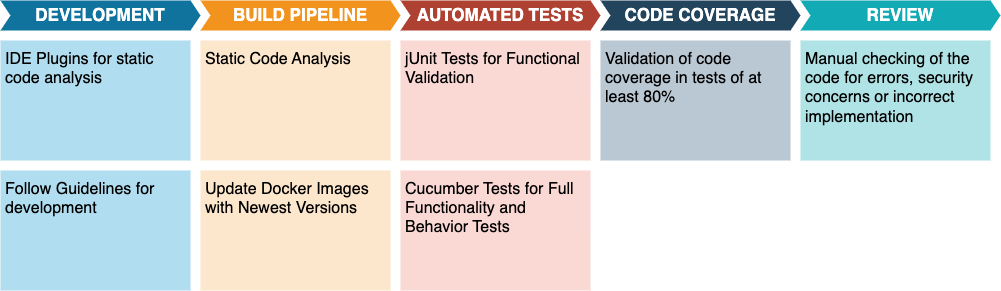
Tools
Tool | Used By | Description |
|---|---|---|
Detekt | IDE, Build Pipeline | Static code analysis of Kotlin Code |
jacoco | Build Pipeline | Ensure test coverage |
OWASP Dependency Check | Build Pipeline | Checks software dependencies for vulnerability |
jk1.dependency-license-report | Build Pipeline | Checks licenses to ensure operational reliability and offers an overview to see used licenses |
Module Security
Methodology | Description |
|---|---|
Security Filter | Filter that ensures that no endpoint can be called without a valid token. |
Secured Endpoints | In principle, all endpoints are secured so that no access can take place without prior authorization. |
Scopes | Scopes are used to check more precise authorizations on the APIs. These are checked for each request using the token. |
Security Tests | Each endpoint is secured by appropriate tests to ensure that access cannot be accidentally compromised. |
OWASP Security Guidelines | All implementations must comply with the OWASP Guidelines. |
Dependency Updates | All dependencies are regularly maintained so that no security gaps can arise from third-party providers or open source projects. |
Docker Image Update | The Docker images are also updated with each build so that Unix security vulnerabilities can be avoided. |
Data Separation / User Data Security | The company's own data models and repositories always ensure that only data belonging to the current user can be loaded. |
No native SQL | To avoid SQL injections, no native statements with unchecked values are used. For data access, |
Security Review Process
A review process has been established to guarantee the security of the server in the long term. This ensures that the security of the software and the components used is reviewed at least once a year.